Of course. "Violent Python" is a well-known and influential book in the cybersecurity and Python programming communities. It's famous for its practical, hands-on approach to learning Python for security tasks.
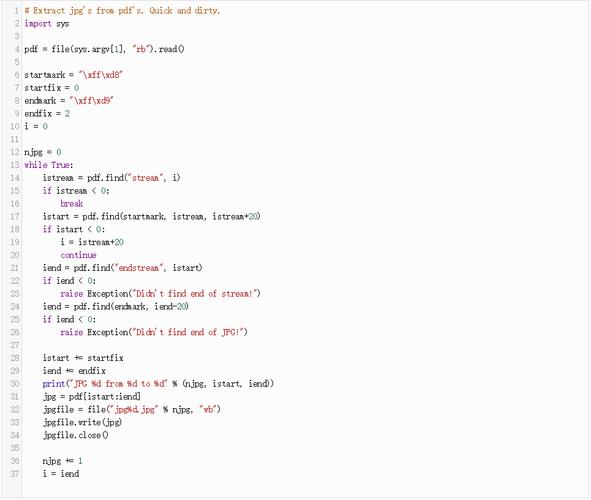
Here is a comprehensive guide to the book, covering its content, how to get it legally, and its alternatives.
What is "Violent Python"?
"Violent Python: A Cookbook for Hackers and Security Analysts" is a book by TJ O'Connor. Unlike traditional Python books that start with "Hello, World," this book dives straight into practical security-related projects using Python.
Core Philosophy: Learn Python by doing. Each chapter presents a specific security problem and walks you through writing a Python script to solve it.
Key Features:

- Project-Based Learning: Each chapter is a self-contained project.
- Practical Focus: Covers real-world tasks like network scanning, password cracking, forensics, and malware analysis.
- Clear Code: The code is well-explained, making it easy to follow the logic.
- Hands-On: Encourages you to run the code and experiment with it yourself.
Table of Contents (What's Inside?)
The book is structured around different domains of security. Here's a breakdown of the topics it covers:
Part 1: Python and Security Fundamentals
- Covers setting up your environment, basic Python syntax, and essential libraries like
Scapyfor network manipulation andPillowfor image processing.
Part 2: Network Tooling and Analysis
- Chapter 1: Port Scanner: Building a port scanner from scratch using raw sockets.
- Chapter 2: SNMP Scanner: Querying SNMP-enabled devices for information.
- Chapter 3: SNMP Community String Cracker: Brute-forcing weak SNMP community strings.
- Chapter 4: Web Crawler: Writing a spider to map out a website's structure.
- Chapter 5: Network Packet Sniffer: Creating a basic packet sniffer to analyze network traffic.
- Chapter 6: ARP Spoofer: Implementing an Address Resolution Protocol spoofer to perform man-in-the-middle attacks.
- Chapter 7: DHCP Starvation: Exhausting a DHCP server's IP address pool.
- Chapter 8: Detecting ARP Spoofing with Scapy: Writing a script to detect the attacks you learned to create.
- Chapter 9: Building a Wireless Scanner: Using Python and the
scapylibrary to find wireless networks.
Part 3: Web-Based Tools and Analysis

- Chapter 10: Web Application Fuzzer: Automating the discovery of vulnerabilities in web apps.
- Chapter 11: Web Application Crawler: A more advanced web crawler that respects
robots.txtand handles logins. - Chapter 12: Web Application Vulnerability Scanner: A basic scanner to find common vulnerabilities like SQL injection and XSS.
- Chapter 13: Google Hacking: Using the Google API to find vulnerable systems based on search queries.
Part 4: Cryptography and Process Injection
- Chapter 14: Packet Forging: Creating custom network packets.
- Chapter 15: Cryptography with Python: Implementing and breaking ciphers like Caesar, Vigenère, and XOR.
- Chapter 16: Cryptography with PyCrypto: Using a robust library for symmetric and asymmetric encryption.
- Chapter 17: Password Cracking: Building a dictionary-based password cracker for various hash types.
- Chapter 18: Process Injection: Injecting code into a running process (a more advanced topic).
Part 5: Malware and Forensics
- Chapter 19: Malware Analysis: Analyzing a simple piece of malware written in Python.
- Chapter 20: Forensics: Using Python to carve files from disk images and analyze PDF metadata.
- Chapter 21: Steganography: Hiding data within images.
- Chapter 22: Reverse Engineering: Using Python to interact with the Ghidra reverse engineering tool.
How to Get the "Violent Python" PDF
It is crucial to obtain the book legally and ethically. The author, TJ O'Connor, put a lot of effort into creating this resource.
✅ Legal and Recommended Method: Purchase the Book
The best way to support the author and get the most up-to-date version is to purchase it. Buying the book often gives you access to a legal digital copy (PDF/ePub) through platforms like:
- Amazon Kindle: You can buy the Kindle version and use the free Kindle app on any device to read it.
- The No Starch Press Website: The publisher, No Starch Press, often sells the ebook directly.
- Other Online Retailers: Google Play Books, Apple Books, etc.
Why buy it?
- Support the Author: It compensates TJ O'Connor for his work.
- Latest Edition: You get the most current and corrected version.
- Legal and Safe: No risk of malware from unofficial sources.
⚠️ Unofficial Sources (Use with Extreme Caution)
You may find websites offering free PDFs of "Violent Python." Be very wary of these for several reasons:
- Copyright Infringement: Distributing copyrighted material without permission is illegal.
- Malware and Viruses: Many of these sites are riddled with malicious ads, pop-ups, and downloadable files that can infect your computer.
- Poor Quality: The files are often low-quality scans with missing pages, blurry text, and incorrect formatting.
- Outdated Content: You might be getting an old, outdated version of the book that contains bugs or deprecated code examples.
Conclusion: While you can find the PDF unofficially, the safest, most ethical, and most beneficial option is to purchase the book.
Alternatives to "Violent Python"
If you're looking for similar books or resources, here are some excellent alternatives:
For a Similar Project-Based Approach:
- Black Hat Python: Python Programming for Hackers and Pentesters by Justin Seitz: This is the most common "competitor" to "Violent Python." It's also project-based and focuses on lower-level topics like writing exploits, trojans, and fuzzers. It's considered a bit more advanced.
- Python for Offensive PenTest: A Practical Guide to Penetration Testing by Hussam Khrais: A more modern take on the same concept, often praised for its clear explanations and up-to-date examples.
For Learning Python for Security (More Structured):
- Mastering Python for Networking and Security by José Manuel Ortega: A great book that builds a strong foundation in Python first and then applies it to networking and security tasks.
- Learning Python for Forensics by Cameron-Hollister, Harrington, and Case: Focuses specifically on using Python for digital forensics, a very in-demand skill.
For Free Online Learning:
- SANS SEC560: Python for Security Professionals: This is a top-tier, paid course, but it's the gold standard for learning Python in a security context. They often have free webinars and sample materials.
- Cybrary.it / TryHackMe / Hack The Box: These platforms have learning paths and modules that incorporate Python scripting into their hands-on labs.
- GitHub: Search for "offensive python scripts" or "security python tools." You'll find thousands of open-source projects to learn from.
Summary
| Feature | Description |
|---|---|
| Book | Violent Python: A Cookbook for Hackers and Security Analysts by TJ O'Connor |
| Focus | Practical, hands-on Python projects for security tasks (networking, web, crypto, forensics). |
| Best Way to Get | Purchase it legally from Amazon, No Starch Press, or other retailers to support the author and get a quality, updated copy. |
| Alternatives | Black Hat Python, Python for Offensive PenTest, and various online courses and platforms. |