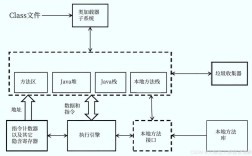
Of course! Let's break down JSESSIONID in Java, covering what it is, how it works, why it's used, and common issues developers face.
What is JSESSIONID?
JSESSIONID is the name of a cookie that Java web applications (built on technologies like Servlets and JSP) use to manage HTTP sessions.
- It's a Session Identifier: Think of it as a unique "key" or "name tag" for a user's session on the server.
- It's a Cookie: By default, this identifier is stored in the user's browser as a cookie. Every subsequent request from that browser to the same server will automatically include this cookie.
- It's Not a User Identifier: It's important to remember that
JSESSIONIDidentifies a session, not necessarily a specific user. A single user can have multiple sessions (e.g., if they log in from two different browsers).
How Does It Work? (The Lifecycle)
Here's the step-by-step process of how JSESSIONID facilitates session management:
Step 1: The First Request
- A user makes their first request to a Java web application (e.g.,
http://example.com/index.jsp). - The server has no information about this user. It needs to create a session to store data (like a shopping cart, user login status, etc.).
- The server generates a unique, random string (e.g.,
A9B8C7D6E5F4G3H2). - The server creates a new session object in memory and maps this unique ID to it.
- The server sends back an HTTP response to the browser, which includes a
Set-Cookieheader:Set-Cookie: JSESSIONID=A9B8C7D6E5F4G3H2; Path=/; HttpOnlyJSESSIONID=A9B8C7D6E5F4G3H2: This is the key-value pair. The name isJSESSIONID, and the value is the unique ID.Path=/: This tells the browser to send the cookie with requests to any path on this domain.HttpOnly: This is a security flag that prevents client-side JavaScript from accessing the cookie, helping to mitigate cross-site scripting (XSS) attacks.
Step 2: Subsequent Requests
- The browser receives this response and stores the
JSESSIONIDcookie. - When the user makes another request to the same server (e.g., to add an item to their cart), the browser automatically includes the cookie in the request headers:
GET /add-to-cart.jsp HTTP/1.1 Host: example.com Cookie: JSESSIONID=A9B8C7D6E5F4G3H2 - The server's application server (like Tomcat, Jetty, or WildFly) sees the
JSESSIONIDcookie in the request. - It looks up the session object associated with
A9B8C7D6E5F4G3H2from its internal map. - The application can now access and modify the session data (e.g., add the new item to the cart stored in the session).
Step 3: Session Timeout or Invalidation
- Timeout: If the user is inactive for a certain period (configured in
web.xml, e.g., 30 minutes), the server will automatically discard the session object to free up memory. The next request from the user will result in a new session and a newJSESSIONID. - Invalidation: The application can explicitly invalidate the session (e.g., when a user logs out). This destroys the session data, and the
JSESSIONIDbecomes invalid.
Where is JSESSIONID Used?
Any Java web application that needs to maintain state between HTTP requests uses JSESSIONID. Common use cases include:
- User Authentication: Storing the logged-in user's object or ID in the session.
- Shopping Carts: Keeping track of items a user has added.
- Preferences: Storing a user's language, theme, or other settings.
- Security Tokens: Storing CSRF tokens or other security-related information.
How to Work with Sessions in Java Code
In a Servlet or JSP, you interact with the session object, not directly with the JSESSIONID string.
In a Servlet:
import javax.servlet.ServletException;
import javax.servlet.annotation.WebServlet;
import javax.servlet.http.HttpServlet;
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletResponse;
import javax.servlet.http.HttpSession;
import java.io.IOException;
@WebServlet("/session-example")
public class SessionExampleServlet extends HttpServlet {
protected void doGet(HttpServletRequest request, HttpServletResponse response) throws ServletException, IOException {
// Get the current session. If it doesn't exist, create a new one.
HttpSession session = request.getSession();
// You can get the session ID programmatically
String sessionId = session.getId();
System.out.println("Current Session ID: " + sessionId);
// Set an attribute in the session
session.setAttribute("username", "john_doe");
// Get an attribute from the session
String user = (String) session.getAttribute("username");
System.out.println("Username from session: " + user);
// Invalidate the session (logout)
// session.invalidate();
response.getWriter().println("Session information has been set.");
}
}
In a JSP:
JSP makes it even easier with implicit objects.
<%@ page contentType="text/html;charset=UTF-8" language="java" %>
<html>
<head>Session Example</title>
</head>
<body>
<h1>JSP Session Example</h1>
<%-- Get the session ID --%>
<p>Session ID: <%= session.getId() %></p>
<%-- Set a session attribute --%>
<%
session.setAttribute("product", "Laptop");
%>
<%-- Get a session attribute --%>
<p>Product in your cart: <%= session.getAttribute("product") %></p>
</body>
</html>
Common Problems and Solutions
Problem 1: JSESSIONID Changes After a Redirect
Symptom: You log in and get a JSESSIONID. You are redirected to a welcome page, but the JSESSIONID has changed. Your session data is lost.
Cause: This is almost always caused by a URL Rewriting fallback mechanism. If the browser has cookies disabled, the server cannot use the JSESSIONID cookie. To maintain the session, it appends the session ID to all URLs in the response as a query parameter, like ;jsessionid=.... If your application generates a hard-coded URL in a redirect, the server won't have a chance to rewrite it, and the session is lost.
Solution: Never use hard-coded URLs in redirects or forwards. Always use the methods provided by the HttpServletRequest object to let the server handle URL rewriting for you.

Bad (Hard-coded URL):
// WRONG: This will break if cookies are disabled
response.sendRedirect("http://example.com/welcome.jsp");
Good (Using response.encodeRedirectURL):
// CORRECT: The server will append the jsessionid if needed
String welcomeUrl = response.encodeRedirectURL("welcome.jsp");
response.sendRedirect(welcomeUrl);
Problem 2: JSESSIONID in the URL (URL Rewriting)
Symptom: You see ;jsessionid=... at the end of your URLs in the browser's address bar.
Cause: This is the fallback mechanism mentioned above. It happens because the browser has disabled cookies. While this ensures the application works, it's undesirable because:
- It exposes the session ID in browser history, server logs, and the Referer header of other sites.
- It can cause problems with browser bookmarks and sharing links.
Solution: Advise users to enable cookies in their browser. There is no way for the server to force this.
Problem 3: Session Fixation Attack
Symptom: An attacker can hijack a user's session.
Cause: An attacker learns a user's JSESSIONID (e.g., through a non-HTTPS link) and forces the user's browser to use that known session ID. If the application doesn't issue a new session ID after the user authenticates (e.g., logs in), the attacker can impersonate the user.
Solution: Always invalidate the old session and create a new one after a user successfully authenticates.
HttpSession oldSession = request.getSession(false); // false = don't create if not exists
if (oldSession != null) {
oldSession.invalidate(); // Destroy the old session
}
HttpSession newSession = request.getSession(true); // Create a new, clean session
// ... proceed with login ...
Summary Table
| Aspect | Description |
|---|---|
| What it is | The name of the session cookie used by Java web applications. |
| Purpose | To link a series of HTTP requests from the same client to a server-side session object. |
| Mechanism | The server sends a Set-Cookie header with a unique ID. The browser sends it back on subsequent requests. |
| Alternatives | URL Rewriting (appending ;jsessionid=... to URLs) as a fallback if cookies are disabled. |
| Key Methods | request.getSession(), session.getId(), session.setAttribute(), response.encodeURL() |
| Security | Can be vulnerable to session fixation and XSS if not handled correctly (use HttpOnly and Secure flags). |