Of course! Let's dive deep into setAccessible() in Java. This is a powerful but often misunderstood method that plays a crucial role in advanced Java programming, particularly in frameworks and libraries.

What is setAccessible()?
setAccessible() is a method of the java.lang.reflect.AccessibleObject class. This class is the superclass for Field, Method, and Constructor objects, which are used for reflection.
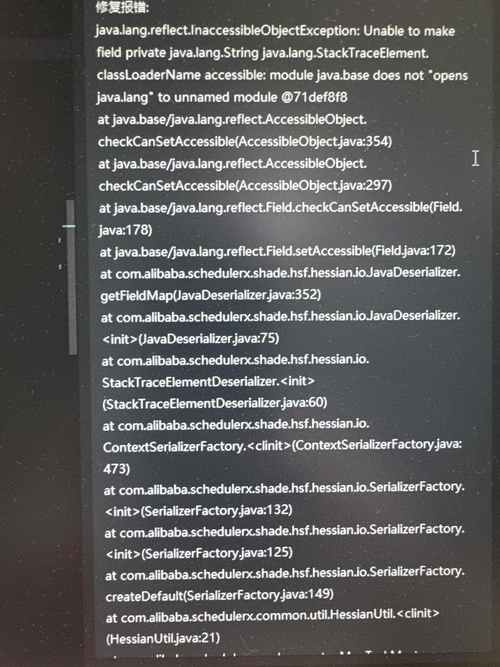
In simple terms, setAccessible(true) bypasses the access control checks performed by the Java Virtual Machine (JVM). By default, the JVM enforces access modifiers like private, protected, and package-private. If you try to access a private member of a class using reflection without setAccessible(), you'll get an IllegalAccessException.
Calling setAccessible(true) on a reflected object tells the JVM: "I know this member is private/protected, but I give you permission to access it anyway. Ignore the access control rules."
The Core Problem: Access Control in Reflection
To understand why setAccessible() is needed, let's look at the problem it solves.

Consider this simple class:
public class Employee {
private String secretId;
public Employee(String secretId) {
this.secretId = secretId;
}
public String getPublicInfo() {
return "This is public info.";
}
}
Now, let's try to access the secretId field using reflection:
import java.lang.reflect.Field;
public class ReflectionDemo {
public static void main(String[] args) {
try {
Employee emp = new Employee("XYZ-123");
Class<?> clazz = emp.getClass();
// Get the private field 'secretId'
Field secretIdField = clazz.getDeclaredField("secretId");
// This line will throw an IllegalAccessException!
String secretValue = (String) secretIdField.get(emp);
System.out.println("Secret ID: " + secretValue);
} catch (NoSuchFieldException | IllegalAccessException e) {
e.printStackTrace();
}
}
}
Output:
java.lang.IllegalAccessException: Class ReflectionDemo cannot access a member of class Employee with modifiers "private"
at java.base/jdk.internal.reflect.Reflection.newIllegalAccessException(Reflection.java:392)
at java.base/java.lang.reflect.AccessibleObject.checkAccess(AccessibleObject.java:349)
at java.base/java.lang.reflect.Field.checkAccess(Field.java:1029)
at java.base/java.lang.reflect.Field.get(Field.java:394)
at ReflectionDemo.main(ReflectionDemo.java:12)The JVM correctly prevents the access because secretId is private. This is where setAccessible() comes to the rescue.
How to Use setAccessible()
The solution is to call setAccessible(true) on the Field, Method, or Constructor object before attempting to access it.
Here is the corrected code:
import java.lang.reflect.Field;
public class ReflectionDemoFixed {
public static void main(String[] args) {
try {
Employee emp = new Employee("XYZ-123");
Class<?> clazz = emp.getClass();
Field secretIdField = clazz.getDeclaredField("secretId");
// THE KEY LINE: Bypass access control
secretIdField.setAccessible(true);
// Now this works without an exception
String secretValue = (String) secretIdField.get(emp);
System.out.println("Secret ID: " + secretValue); // Output: Secret ID: XYZ-123
// You can also set the value of a private field
secretIdField.set(emp, "ABC-789");
System.out.println("New Secret ID: " + secretValue); // Output: New Secret ID: ABC-789
System.out.println("New Secret ID from object: " + emp.getPublicInfo()); // Note: getPublicInfo() doesn't show it
} catch (NoSuchFieldException | IllegalAccessException e) {
e.printStackTrace();
}
}
}
Output:
Secret ID: XYZ-123
New Secret ID: ABC-789
New Secret ID from object: This is public info.Security Manager and setAccessible(true)
The behavior of setAccessible() is controlled by the Java Security Manager.
-
When a Security Manager is NOT active (most common development environments):
setAccessible(true)will always succeed. You can bypass any access modifier.
-
When a Security Manager IS active (e.g., in a Java applet, enterprise application server, or when running with a security policy file):
- The ability to use
setAccessible()is governed by aReflectPermissionpermission. - By default, code running under a security manager does not have this permission.
- If you try to call
setAccessible(true)without the proper permission, you will get aSecurityException.
- The ability to use
Example of a Security Policy File (java.policy):
This grants the permission to a specific codebase.
grant codeBase "file:/path/to/your/application/classes/" {
permission java.lang.reflect.ReflectPermission "suppressAccessChecks";
};Without this permission, the ReflectionDemoFixed code would fail with:
java.security.AccessControlException: access denied ("java.lang.reflect.ReflectPermission" "suppressAccessChecks")Common Use Cases
setAccessible() is not just a "hack" to break encapsulation. It has legitimate and essential uses:
-
Testing Private Methods/Fields: This is the most common use case. Unit testing frameworks like JUnit and Mockito rely heavily on
setAccessible()to test the internal state of a class or to mock private methods.- Example: You want to verify that a private helper method was called correctly or to set a private field to a specific state before a test runs.
-
Dependency Injection Frameworks (e.g., Spring, Guice): These frameworks need to inject dependencies into fields or methods that are marked as
@Autowiredor@Inject, even if they areprivate. They use reflection andsetAccessible()to perform this injection. -
Object-Relational Mapping (ORM) Frameworks (e.g., Hibernate, JPA): ORM frameworks map database columns to object fields. Often, these fields are made
privateto protect the object's integrity. The framework uses reflection to read and write these private fields to synchronize the object with the database. -
Serialization/Deserialization: Libraries that convert objects to and from formats like JSON or XML (e.g., Jackson, Gson) need to access all fields of an object, including private ones, to read and write their values.
-
Legacy Code Analysis: When working with old code where you don't have control over the source, you might need to use reflection and
setAccessible()to understand or debug its internal state.
Performance Considerations
Using reflection, and setAccessible() in particular, has a performance overhead compared to direct method/field access.
- Initial Cost: The first time you call a method or access a field via reflection, the JVM performs security checks and other setup, which is slower.
setAccessible()Cost: The call tosetAccessible(true)itself has a small cost.
Mitigation: To improve performance, you can cache the Field, Method, or Constructor objects after you've obtained them and called setAccessible(true). This way, the expensive lookup and permission check only happens once.
Best Practices and Warnings
-
Last Resort:
setAccessible()should be used as a last resort. It breaks the fundamental principle of encapsulation in object-oriented programming. If you find yourself needing to access private members frequently, consider if your class design is flawed. Could the private member be madeprotected? Could you provide a public getter/setter? -
Use with Caution: Modifying the internal state of an object via reflection can lead to unpredictable behavior and bugs that are very difficult to trace. You are bypassing the object's own logic and contracts.
-
Security Implications: In security-sensitive applications, be extremely careful. Malicious code could potentially use reflection to expose or modify sensitive data if it can get a hold of your objects.
Summary
| Feature | Description |
|---|---|
| What it is | A method on Field, Method, and Constructor objects used in Java reflection. |
| What it does | Bypasses JVM access control checks, allowing access to private, protected, and package-private members. |
| Why it's needed | By default, reflection respects access modifiers. setAccessible() is the override switch. |
| Security | Requires suppressAccessChecks ReflectPermission if a SecurityManager is active. |
| Use Cases | Testing, Dependency Injection, ORM, Serialization, and analyzing legacy code. |
| Performance | Slower than direct access. Cache reflected objects to mitigate this. |
| Warning | Breaks encapsulation. Use sparingly and be aware of the risks. |